Stay ahead of security threats
AI-based XDR to reduce false positives, resolve threats in real-time before they become issues, no need to invest in expensive and hard-to-find HR resources
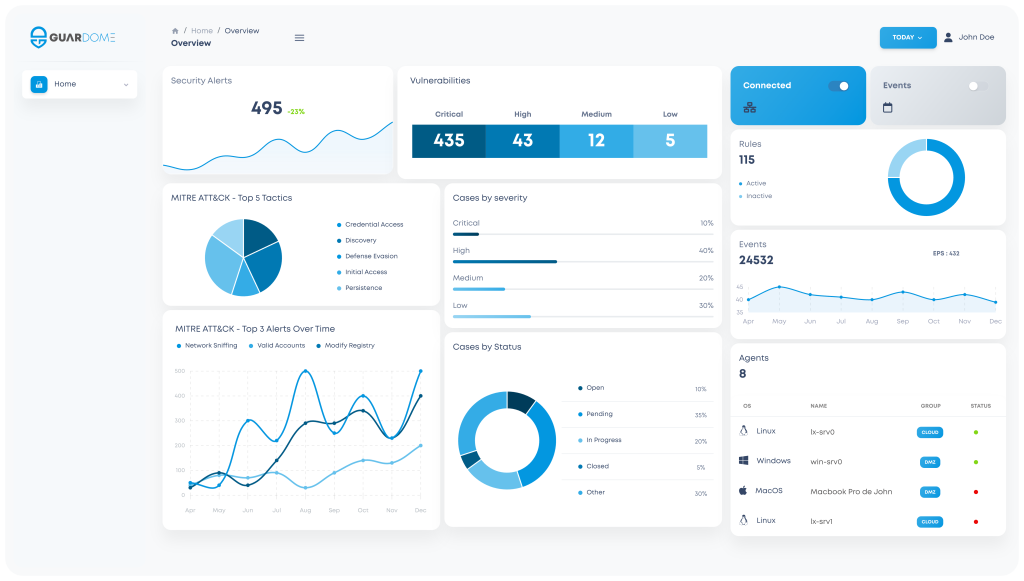
Ensuring the protection of your expanding organization from cyber threats is of utmost importance. However, this endeavor consumes valuable time and resources that could be better allocated towards growth-oriented activities. Whether your business operates with a solitary IT infrastructure or possesses a security team that is enhancing its capabilities and assets, Guardome provides you with the means to monitor, gather, and analyze data throughout your network, spanning from devices to server files.
Equipped with an advanced machine learning multi-step attack hunting engine, real-time alerts, and constant tracking of every piece of data, our autonomous detection and response XDR solution serves as the sole technology necessary to safeguard your assets and maintain the security of your business.
By leveraging our solution, we effectively assess the vulnerabilities within your organization and employ Guardome AI-driven to detect potential threats. This intelligent system autonomously cross-references these vulnerabilities with established attack vectors, enabling analysts to swiftly identify attacks and implement prompt mitigation and response measures.
Adeptly handles events related to the prevention of cyber attacks with superior accuracy, depth, and speed compared to humans. This enhanced capability translates into improved Service Level Agreements for end-users, ensuring a more robust and efficient defense against cyber threats.
Dynamically adapts to evolving threat landscapes, promptly responding to emerging challenges and identifying issues as they arise. It boasts scalability and the ability to adapt to novel forms of attacks, ensuring comprehensive protection against evolving cyber threats
By delegating tasks from costly cybersecurity analysts, our solution significantly enhances the operational return on investment (ROI) of the Security Operations Center (SOC). This effectively reduces the workload on analysts, allowing them to focus on more critical and complex security matters.
Effortlessly implement our solution within a matter of hours, choosing from a range of non-intrusive options such as agentless, agent-based, or a hybrid deployment approach.
Effortlessly implement our solution within a matter of hours, choosing from a range of non-intrusive options such as agentless, agent-based, or a hybrid deployment approach.



Consolidate and streamline your cybersecurity operations by minimizing the number of disparate applications utilized, and instead, adopt a comprehensive end-to-end solution that optimizes the productivity of your Security Operations Center (SOC).
Consolidate and streamline your cybersecurity operations by minimizing the number of disparate applications utilized, and instead, adopt a comprehensive end-to-end solution that optimizes the productivity of your Security Operations Center (SOC).


Achieve substantial enhancements in cyber defenses and threat intelligence, continuously fortifying your security posture while delivering accurate and actionable insights across all levels of your organization.



Achieve substantial enhancements in cyber defenses and threat intelligence, continuously fortifying your security posture while delivering accurate and actionable insights across all levels of your organization.



Guardome seamlessly integrates multiple cybersecurity engines and tools, encompassing vital aspects of network security within a unified platform that provides a cohesive defense strategy.


Guardome seamlessly integrates multiple cybersecurity engines and tools, encompassing vital aspects of network security within a unified platform that provides a cohesive defense strategy.


Here are just few reasons why us





Let’s explore how we can apply our technology to fit your Cybersecurity needs. You will be completely satisfied with our fast and efficient service
Input your search keywords and press Enter.